Welcome to the Web3 world, where digital finance and applications are shown in a revolutionary way through the fusion of blockchain technology, cryptocurrencies, and a pioneering spirit. Are you overwhelmed by the wealth of terms in the Web3 world that you don’t understand? Are those slangs barriers for you to learn about Web3? Don’t worry! We’re here to explain the obscure terms to guide your learning. Today, we're diving into an exciting development in the world of Web3: [Verifiable Computation].
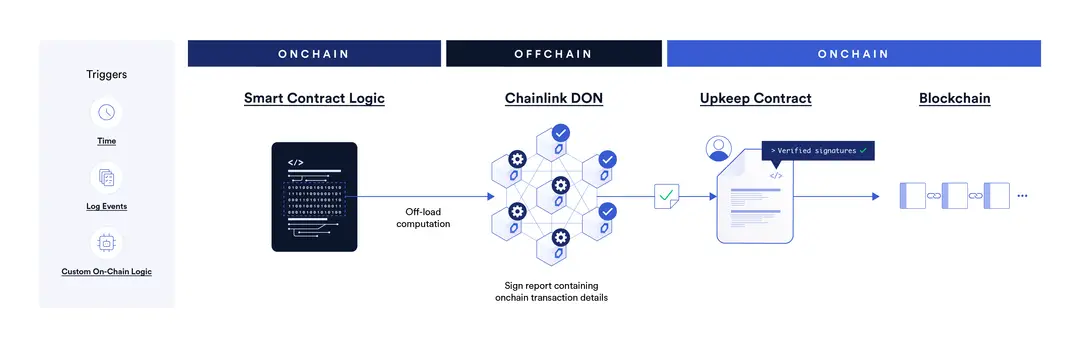
Verifiable computation is a cryptographic process that allows a party (the verifier) to efficiently check the correctness of the output of a computation performed by another party (the prover) without having to execute the computation themselves. This is particularly useful in environments where resources are limited, or trust is scarce. In blockchain and Web3 applications, verifiable computation enables decentralized networks to offload complex computations to external, more capable systems without sacrificing security or trustworthiness. It ensures that the computation has been carried out correctly, preserving integrity and enhancing scalability across distributed networks.
The core idea behind verifiable computation lies in the interaction between the prover and the verifier:
1.The Computation Task: A user or a smart contract specifies a task that requires significant computational resources.
2.The Prover's Role: An external prover, which can be a powerful server or a dedicated computation service, performs the required computation and generates a proof of correctness.
3.Generating the Proof: The proof is created using cryptographic techniques that may involve complex algorithms depending on the type of verifiable computation protocol used (e.g., zk-SNARKs, STARKs).
4.The Verifier's Role: The verifier, which can be a smart contract or another participant in the blockchain network, checks the proof provided by the prover. This verification process is designed to be much less resource-intensive than performing the computation itself.
5.Accepting or Rejecting the Computation: If the proof is valid, the computation is accepted; otherwise, it is rejected.
In scenarios where computations need to be outsourced to cloud providers, verifiable computation ensures that the cloud executes tasks correctly and does not return false or manipulated results, thus maintaining the integrity of data and computations.
Verifiable computation can be employed to perform data analyses on encrypted data, ensuring the privacy of sensitive information while still deriving useful insights. This is crucial for industries handling private data, such as healthcare and finance. Scalable Blockchain Networks
By enabling off-chain computation, verifiable computation allows blockchain networks to handle more complex applications without overloading the main chain. This significantly enhances throughput and efficiency.
Challenges and Future Directions
While verifiable computation opens up a plethora of opportunities, it is not without its challenges. The main issues include the computational overhead associated with generating proofs, especially in dynamic or interactive contexts, and the still-maturing nature of the cryptographic techniques involved.
As research progresses, the focus is on developing more efficient algorithms and protocols that reduce the cost and increase the speed of both proof generation and verification. The future of verifiable computation looks promising, with potential breakthroughs that could further solidify its role in expanding the capabilities of Web3 technologies.
Verifiable computation is a transformative technology in the Web3 landscape, offering a robust method for ensuring the accuracy and integrity of outsourced computations. By mitigating trust issues and reducing the computational load on decentralized networks, it paves the way for more complex and scalable applications. As we continue to navigate the intricacies of blockchain technologies, understanding and implementing verifiable computation will be key to unlocking the full potential of decentralized systems.