Back
Fraud Proof
Linea
By HackQuest
Jun 7,20245 min readWelcome to the Web3 world, where digital finance and applications are shown in a revolutionary way through the fusion of blockchain technology, cryptocurrencies, and a pioneering spirit. Are you overwhelmed by the wealth of terms in the Web3 world that you don’t understand? Are those slangs barriers for you to learn about Web3? Don’t worry! We’re here to explain the obscure terms to guide your learning. Today, we're diving into an exciting development in the world of Web3: [Fraud Proof].
Overview
A fraud proof, also known as fault proof, is evidence presented by a verifier to contest the accuracy of a transaction state. Depending on its design, the fraud proof scrutinizes a subset of transactions to ascertain their validity.
Fraud proofs serve to establish that a state transition was incorrect. They operate on a presumption that blocks depict valid L2 data states unless demonstrated otherwise. However, in practice, a block that has been committed could potentially include an incorrect state transition.
Simple explanation: If the fraud proof identifies a problem, the transactions in the batch are discarded, and the batch reverts to a previously confirmed valid state. Conversely, if no fraud proofs are submitted during the challenge period, the state change is assumed to be accurate.

Source: Blockworks
How It Works
Fraud proofs operate by contrasting Merkle roots and confirming the initial and final state roots through either a one-time computation process (as seen with Optimism) or a multi-stage computation process (as used by Arbitrum).
The blockchain utilizes a data structure called a Merkle Tree, where each transaction is stored as a leaf and subsequent branches are formed by progressively intricate hashes of the tree.
The top node, known as the Merkle Root, compresses the data into a hash, which simplifies the process for users by eliminating the need to continuously download the full main chain.
If a verifier decides to contest a transaction state change, they simply have to provide the existing post-state root along with specific segments of the Merkle tree necessary to calculate the accurate post-state root. If there is a discrepancy between the two, the transaction state changes are undone, and the hash is restored to a verifiably accurate state root.
Source: Medium
Benefits
The primary advantage of Fraud Proofs is that they are only necessary when there is a suspected error in the state transition, rather than for every change. This makes them less demanding on computational resources and more appropriate for environments where scalability is constrained.
Fraud Proofs VS Validity Proofs

Source: Orochi Network
Similarities
1.Both are Utilized in Layer 2, Rollup-Based Solutions to Enhance Scalability
2.Multiple Implementations for Validity Proofs and Fraud Proofs. Validity proofs include various implementations such as SNARKs and STARKs, whereas fraud proofs are implemented in forms like single rollups and multi-round rollups.
3.Single vs. Multi-Round Rollups
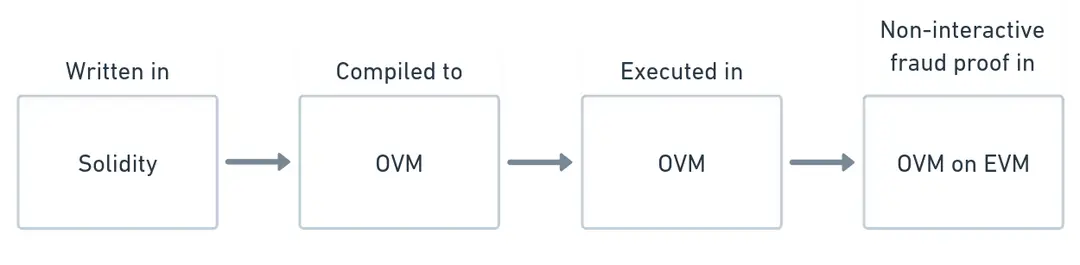
Optimistic rollups primarily come in two forms: single and multi-round rollups, which are implemented by Optimism and Arbitrum, respectively. In the case of Optimism, when a verifier presents a fraud proof to contest a transaction, the entire proof is executed on the EVM, a process that is straightforward and swift, only constrained by a dispute time delay (DTD) of one week.
Conversely, Arbitrum’s approach to fraud proof verification involves an interactive off-chain dispute resolution process. Here, the asserter and the challenger iteratively refine the focus of the transaction in several rounds until they pinpoint a segment where they differ.
Differences
1.Validity Proofs Require More Computational Effort Than Fraud Proofs
Zero-knowledge (ZK) proofs involve complex mathematical validations and generally demand significant computational resources due to the intricacies of ensuring a truly zero-knowledge verification process. Fraud proofs are less expensive per batch, costing about 40,000 gas, compared to ZK SNARK proofs that need around 500,000 gas. Nonetheless, ZK SNARKs tend to be more cost-effective on-chain since optimistic rollups must relay all data back to the main blockchain for fraud proofs to validate or invalidate a result.
2.Validity Proofs Provide Immediate Validation, Fraud Proofs Include a Delay
A key distinction between ZK and fraud proofs is the immediacy of transaction validation with ZK proofs, contrasted with the inherent Dispute Time Delay (DTD) associated with fraud proofs, which can decelerate transactions. A batch will only be committed to Ethereum if no fraud proofs are filed by verifiers within the designated timeframe.
3.Validity Proofs Offer Greater Decentralization and Data Security
ZK proofs, which require minimal interaction—merely the submission of a proof to a validator—facilitate a highly decentralized process. Additionally, as these proofs maintain zero knowledge while ensuring precise accuracy, they safeguard user privacy and significantly reduce the risk of major security threats, such as 51% attacks, on the L1 chain. On the other hand, optimistic rollups involve a risk where a fraud proof submitted by a verifier could be intercepted or subjected to a DDoS attack, potentially obstructing a transaction state challenge.
4.Implementing Validity Proofs is More Challenging
While optimistic rollups and their associated fraud proofs are compatible with any Ethereum Virtual Machine (EVM) or Optimistic Virtual Machine (OVM), zero-knowledge proofs and ZK rollups necessitate specialized virtual machines known as zero-knowledge Ethereum Virtual Machines (zkEVMs). These virtual machines are designed to execute smart contracts in a manner that accommodates ZK computations and cryptographic validity proofs.
The Next Step
Arbitrum is constantly planning to optimize the fraud proof process. The Offchain Labs announced the testnet availability of Arbitrum BOLD as another milestone in the evolution of Arbitrum. Read more 👇
Conclusion
Fraud Proofs represent a critical mechanism within the blockchain, primarily serving as a safeguard to ensure the integrity of transactions by allowing any participant to challenge inaccuracies within transaction states. This system is especially pivotal in maintaining the health and accuracy of Layer 2 scaling solutions like rollups, where they help manage the data validation process efficiently and securely.
Fraud Proofs operate by comparing the initial and final states of transactions through a precise verification process using Merkle roots. This method ensures that only the necessary data is processed, thus conserving computational resources and enhancing the scalability of blockchain networks. The beauty of Fraud Proofs lies in their selective application—only activated when discrepancies arise, thereby optimizing the use of resources and ensuring the system’s scalability under restricted conditions.
Moreover, the stark contrast between Fraud Proofs and Validity Proofs highlights the versatility and adaptability of blockchain verification mechanisms. While Fraud Proofs offer a cost-effective and interactive solution for ensuring transaction integrity, Validity Proofs provide a non-interactive, computationally intensive alternative that guarantees immediate transaction validation.
As blockchain technology continues to evolve, the role of Fraud Proofs will be increasingly significant in ensuring the security, efficiency, and reliability of Layer 2 solutions. Their ability to handle disputes effectively not only strengthens trust in decentralized platforms but also reinforces the robust architecture of blockchain technology, making it a cornerstone of future blockchain scalability and security strategies.